In this post, I will guide you through the basic steps for defining a new Service Account and granting different roles on BigQuery through the cloud. It is a common choice to work at the command line and manage development workflow in a terminal window.
Read more: Quick Guide: BigQuery Service Account Setup Using gcloudContents
Setting Up Your Environment with BigQuery Sandbox
The easiest way to follow along with this guide is to use your BigQuery environment.
If you’re new to BigQuery, the BigQuery Sandbox is a great place to start. It’s a free, no-setup-required option that provides limited but sufficient capabilities to complete all the steps in this guide. It allows you to explore BigQuery without incurring any costs.
To get started, visit: https://tinyurl.com/mr27p7cu
You’ll need a Google account to access the sandbox. If you don’t already have one, you’ll need to create it to authenticate with Google Cloud services.
Note: This guide does not cover the steps to set up the BigQuery Sandbox, but the process is simple and well-documented in the linked article. By the end of that setup, you should have access to a functional BigQuery environment with some usage limitations, as outlined by Google.
Here, an example:
Activating Google Cloud Shell and first commands on gcloud
You will have multiple options for executing the gcloud command line, including downloading the gcloud CLI from this link: https://tinyurl.com/28ahf452 . However, we will use Google Cloud Shell, an integrated component that you can access from BigQuery. You have to go to the top right side of your UI and click on the following icon:

Immediately, it should show you
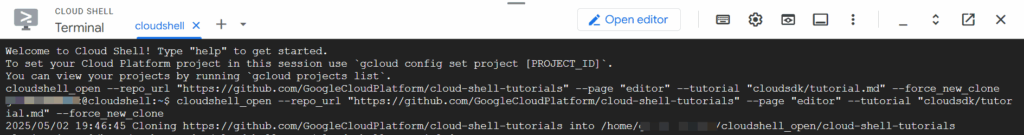
Defining the project
To start interacting with the project, we must set up with the following command
|
1 |
gcloud config set project [PROJECT_ID] |
The Project_Id can be obtained from BigQuery in the next section, inside the UI
Once you click on the previous section, it should display a window where you can pick up the required project. In my case, due to the Sandbox configuration, I only have one
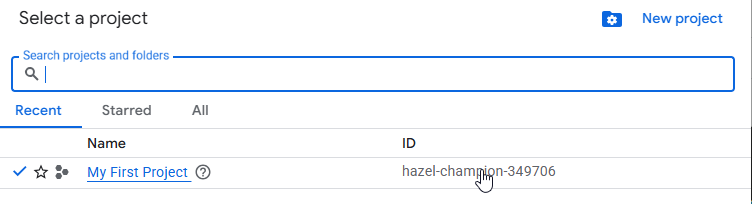
With this information, you could set up the project and continue with the following commands which are intended to create a new Service Account and grant some roles.
Creating a new Service Account
A service account is useful for securely automating access to Google Cloud resources without requiring user interaction. It is recommended that a naming convention at the company level be followed and adhered to. In this example, we are going to create a new one called demo360.
The following code performs two key actions: it creates the service account and assigns it the roles/bigquery.user IAM role to grant appropriate BigQuery access.
|
1 2 3 4 5 6 7 8 9 |
-- Create Service Account gcloud iam service-accounts create demo360-service \ --description="Service account for BigQuery access" \ --display-name="geolab-bq-service-account" -- BigQuery Grant (User) gcloud projects add-iam-policy-binding hazel-champion-349706 \ --member="serviceAccount:demo360-service@hazel-champion-349706.iam.gserviceaccount.com" \ --role="roles/bigquery.user" |
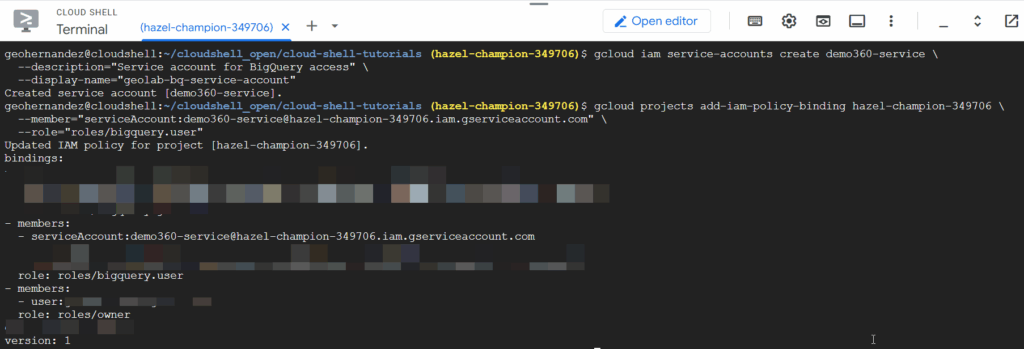
At this point, we can get the JSON file, which contains the detailed information related to the key associated with the service account. Execute the following command:
|
1 2 |
gcloud iam service-accounts keys create key.json \ --iam-account=demo360-service@hazel-champion-349706.iam.gserviceaccount.com |
It would show you a message like this:

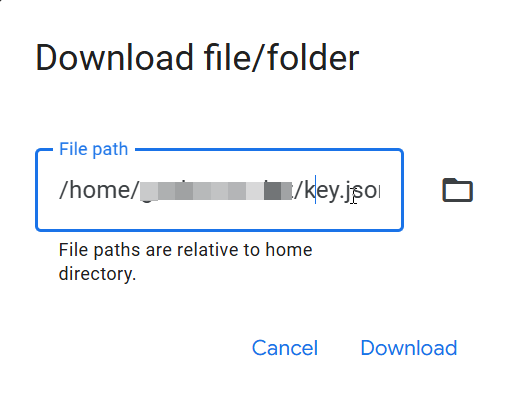
To download the generated key.json, you should go to the BigQuery Cloud Shell Terminal and three dot, and inside it, go to the Download option and explore the file created and stored in your user repository.
Assigning a new role and listing the roles of the Service Account
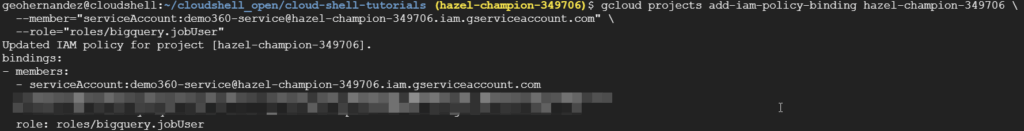
The final part of this article consists of granting a new role to the Service Account and listing the roles assigned to it.
|
1 2 3 4 5 6 7 8 9 10 |
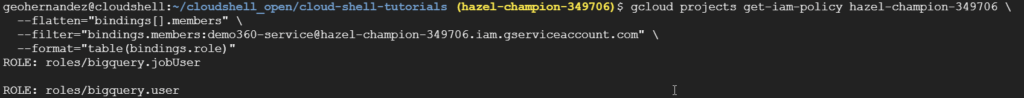
-- BigQuery Grant (Access jobUser) gcloud projects add-iam-policy-binding hazel-champion-349706 \ --member="serviceAccount:demo360-service@hazel-champion-349706.iam.gserviceaccount.com" \ --role="roles/bigquery.jobUser" -- Get the roles associated to a Service Account gcloud projects get-iam-policy hazel-champion-349706 \ --flatten="bindings[].members" \ --filter="bindings.members:demo360-service@hazel-champion-349706.iam.gserviceaccount.com" \ --format="table(bindings.role)" |
Conclusion
In this guide, we covered the essential steps to create a service account and assign BigQuery roles using the gcloud CLI. Using the BigQuery Sandbox allows you to follow along for free, without complex setup.
This approach supports secure, automated access to your data projects. With these basics in place, you’re ready to start building on BigQuery.

